Today’s routers are loaded with features that make them easier for everyday consumers to use. However, some of these features are vulnerable to hackers, so I always turn off these router settings for better security.
1 WPS

Wi-Fi Protected Setup (WPS) sounds like a fantastic idea on paper. It lets you authenticate wireless devices on your network by simply pushing the WPS button on your router. Then, you go to a client device and press its WPS button. Voilà, it’s connected, all without needing to enter a Wi-Fi password.
The ease of WPS is what makes it so tempting—especially if you’re using one of those routers from your ISP that comes with a long and tedious default password. But after learning more about real network security steps, I always disable it in my router’s admin panel.
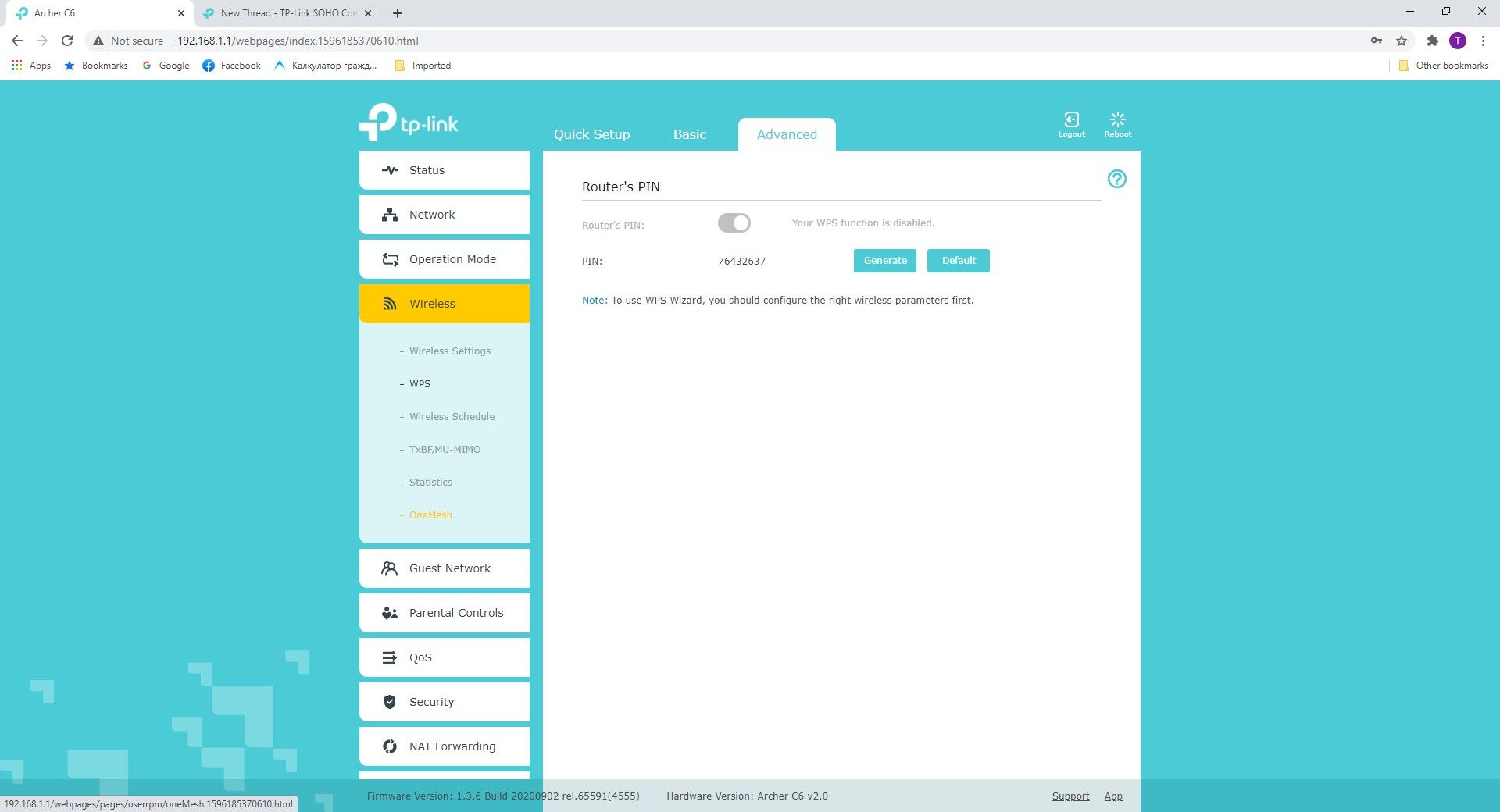
How come? Malicious users can hijack WPS with ease and gain entry to your wireless network. That’s because WPS:
- Communicates via a PIN that’s trivial to brute-force.
- Has vulnerabilities in its design that often don’t get patched.
The better solution is old-fashioned: require a strong Wi-Fi password with WPA2 or WPA3 (if you have a more recent router). These protocols have more difficult-to-crack encryption and security implementations.
2 UPnP
Routers are the gatekeepers to your home network and protect it from the roaming bot gangs of the interwebs. But that protection can be frustrating when it’s overzealous. In the past, multiplayer games often failed to connect if you didn’t open the right ports on your router. Major bummer.
Opening ports correctly was never as straightforward as it sounded. Does the software need a single port or a range? And should they be opened for TCP or UDP?
- Your software asks permission for the ports it needs.
- Your router’s UPnP feature opens these ports automatically.
I had an intense but brief fling with UPnP when it first arrived. But that affair has ended, and I always disable UPnP now. Where did the love go?
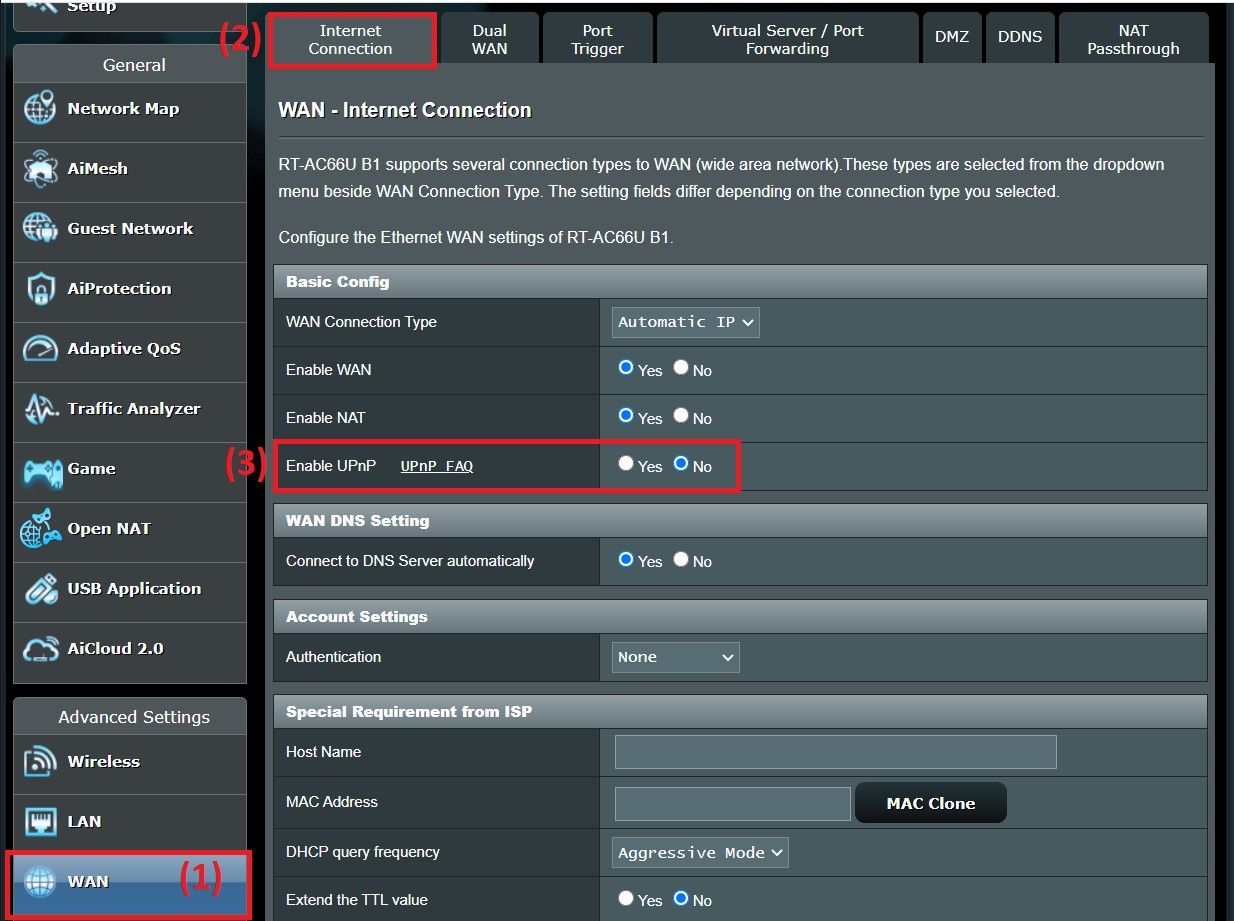
UPnP is dangerous because a rogue program can take advantage of the protocol’s rich feature set to open ports without your knowledge—effectively circumventing the protection of your router’s firewall.
Luckily, most apps today are programmed to function as intended, even when UPnP is disabled. For the few cases that won’t—like accessing your Plex media server away from home—it’s safer to set up a port forwarding rule for only what you need.
3 NAT-PMP
The network engineers at Apple recognized the security risks with UPnP and devised an alternative solution for their apps called Network Address Transversal Port Mapping Protocol. NAT-PMP has a similar goal to UPnP, except that NAT-PMP:
- It is more narrowly focused on port mapping only.
- Has tighter security implementations.
NAT-PMP was first introduced by Apple in 2005. After all this time, the protocol is still only commonly used by Apple software, which is baked into apps like FaceTime. That doesn’t mean only Apple users are affected: NAT-PMP is often enabled by default on many mainstream router brands like ASUS and NETGEAR.
So, did Apple succeed in tightening security with NAT-PMP? To an extent, yes, but it’s still not enough. I always disable NAT-PMP (sometimes listed as “port triggering”), and I recommend you do the same.
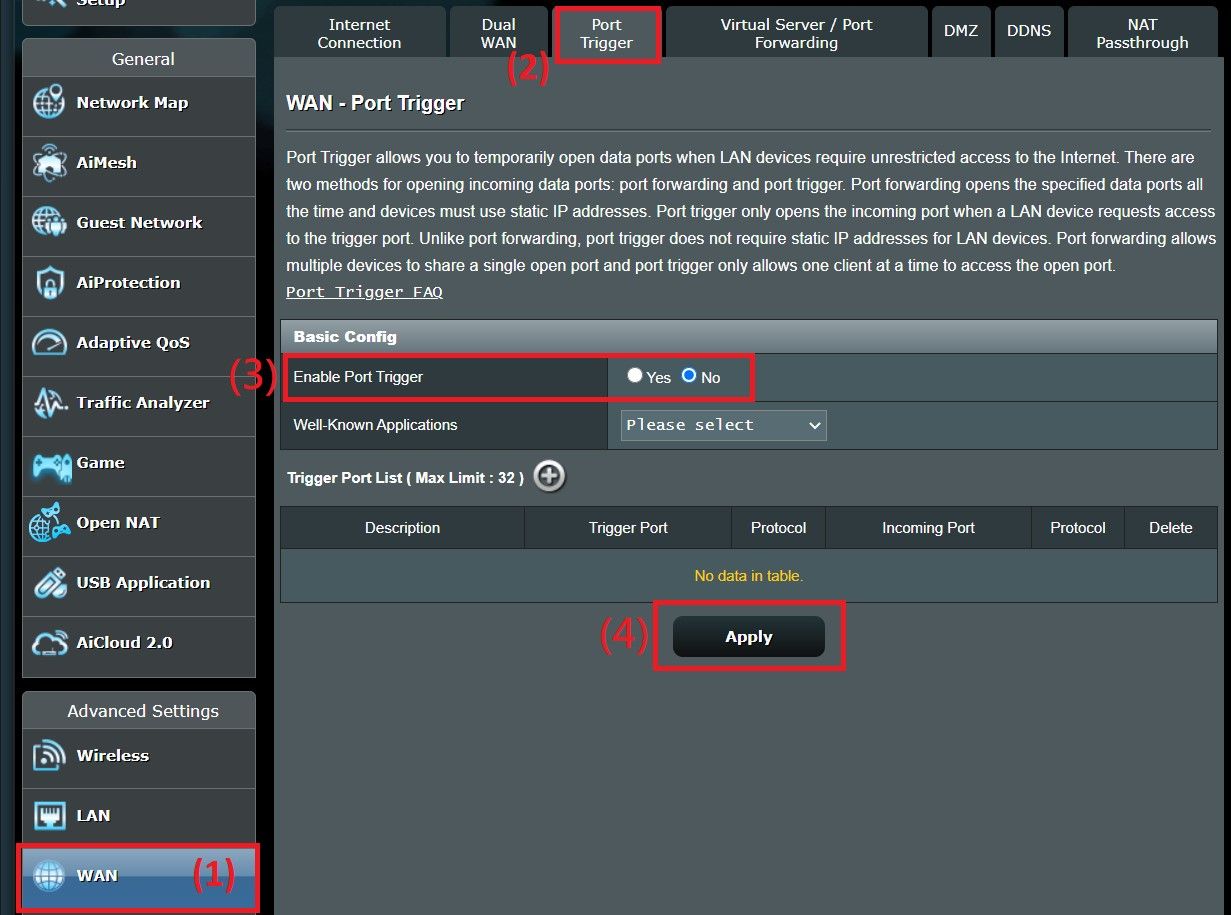
NAT-PMP also uses flawed logic to let apps control which ports to open on your router. This is fine when Apple AirPlay requests it, but it’s not so great when Trojan App XYZ figures out how to fake authentication to get the same privileges.
NAT-PMP security vulnerabilities have affected millions of devices. It’s simply safer to turn the feature off. Even with it disabled, my mobile and Apple TV 4K apps still work just fine. For the rare hiccups, use port forwarding instead.
Maturing into a security-first mindset can sometimes mean giving up what’s easiest. Maybe you’ll decide it’s time to eliminate these three security risks.



0 Comments